Exploiting Web Server Vulnerabilities (Capstone)
Objective
The goal of this lab was to enumerate hidden directories, identify insecure configurations, and exploit the web server to access a hidden flag file.
Environment & Scope
- Target network:
10.5.5.12 - Web servers tested: Apache and other misconfigured services
- Tools used:
gobuster,dirbuster/dirb,dirsearch,nikto - Focus: Directory enumeration, misconfiguration discovery, URL manipulation and sensitive file retrieval
Step 1 — Gobuster Directory Bruteforce
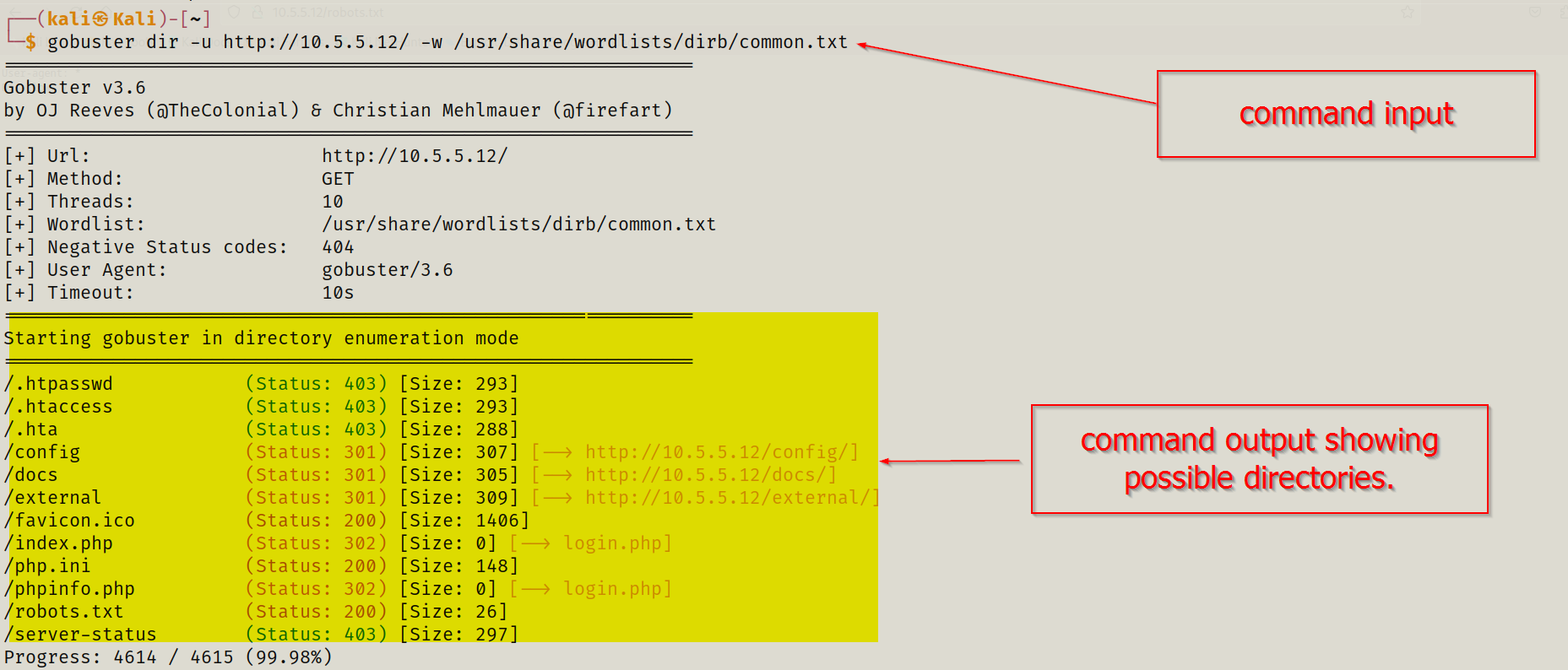
I used Gobuster to discover hidden directories via automated directory bruteforce:
gobuster dir -u http://10.5.5.12/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
This revealed multiple directory paths including config, docs, external, etc.
Step 2 — Verifying Directory Listings using OWASPS Dirbuster
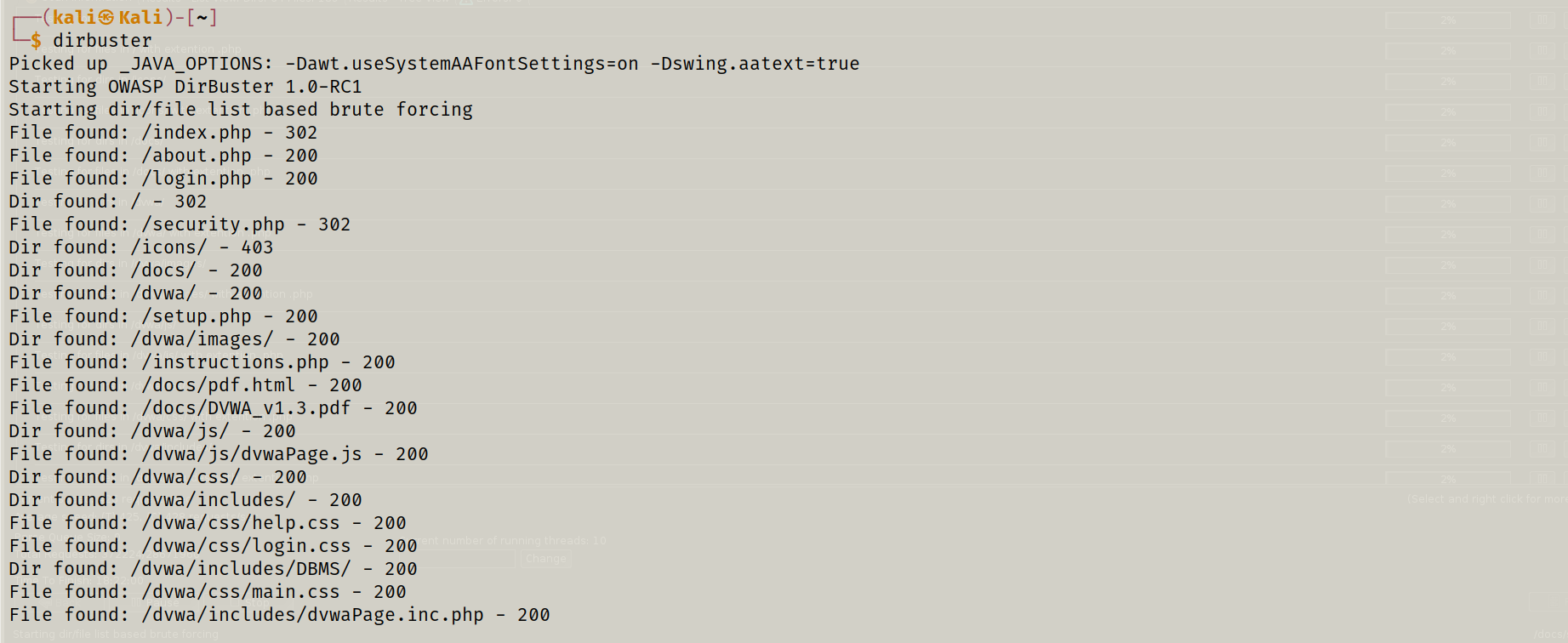
To verify the directory listings, i used Dirbuster :
dirb http://10.5.5.12/ /usr/share/wordlists/dirb/common.txt
This revealed hidden directories such as /security.php, /index.php, and /login.php.
Step 3 — Validating and enumerating further with Dirsearch
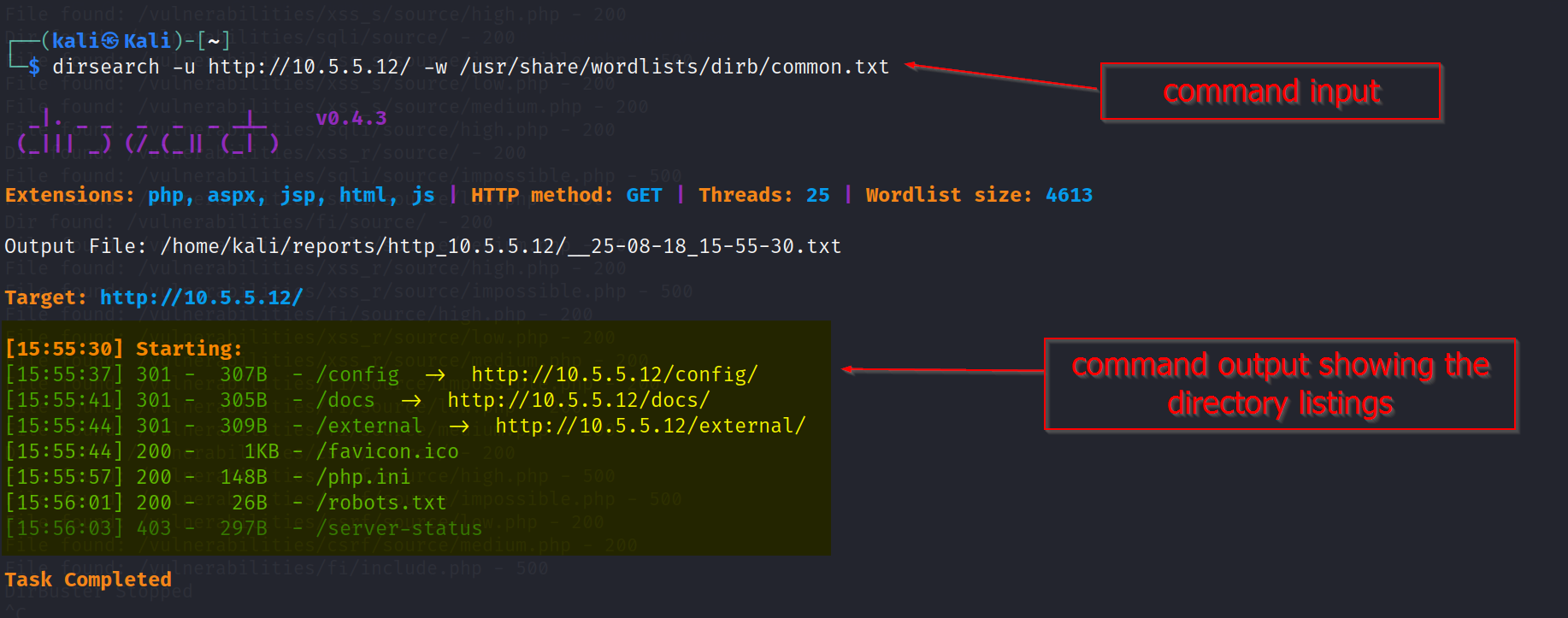
Using dirsearch, i was able to identify directories with possible directory redirects:
dirsearch -u http://10.5.5.12 -w /usr/share/wordlists/dirb/common.txt
This attack revealed directories redirect paths such as /docs, /config, and /external.
Step 4 — Vulnerability Scanning with Nikto
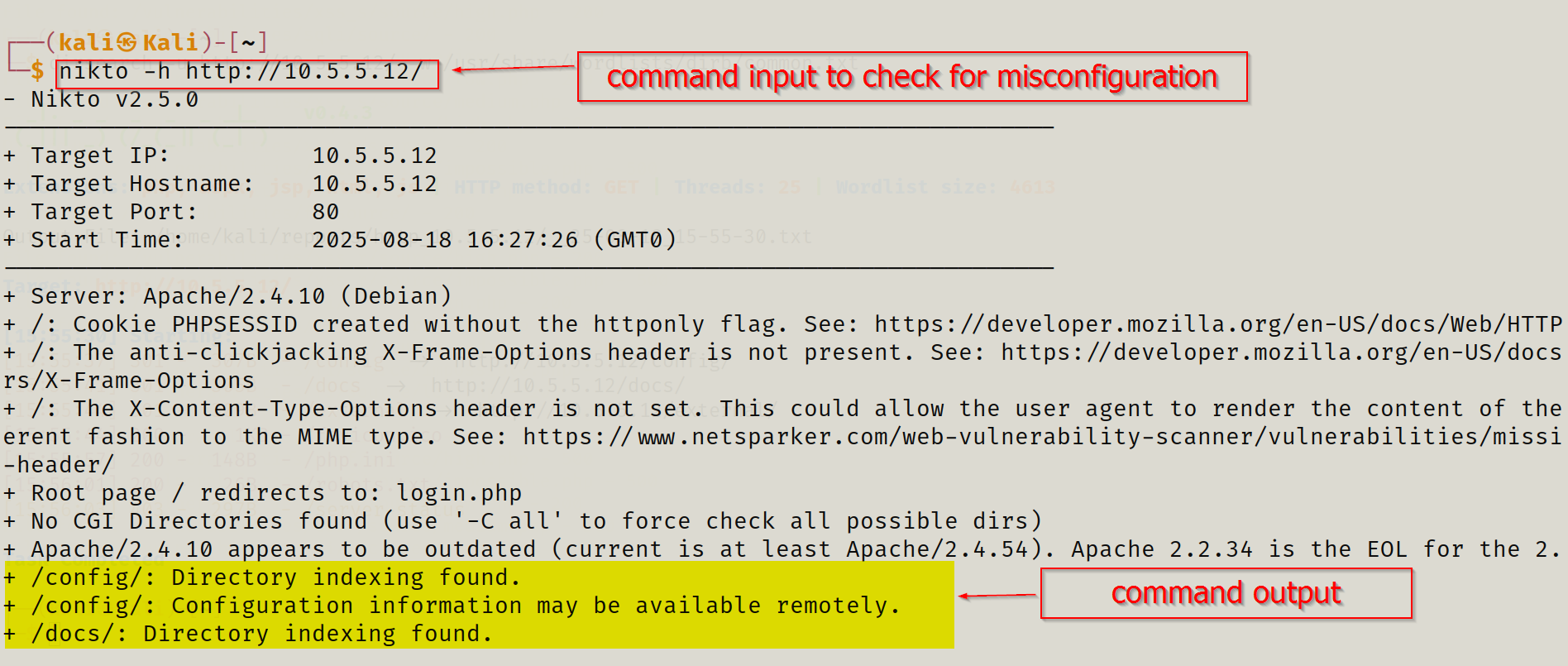
I ran Nikto to identify common misconfigurations and exposures:
nikto -h http://10.5.5.12/
Nikto flagged directory listing, outdated software, and identified a cookie PHPSESSID misconfiguration.
Step 5 — File Upload Vulnerability
Testing the /uploads directory, I attempted to upload a PHP login web shell. To bypass filters, I renamed the file with a double extension:
login.php.png
After uploading, I executed commands on the server through the shell.
Step 6 — Exploring Discovered Directories
By browsing the discovered directories (/docs/, /external/, /config/), I located application files and backup archives. These confirmed misconfigured permissions that allowed directory listing and file retrieval.
Step 7 — Locating Sensitive Files
Within /config/, I found a file db_form.html which contained references to database configuration.
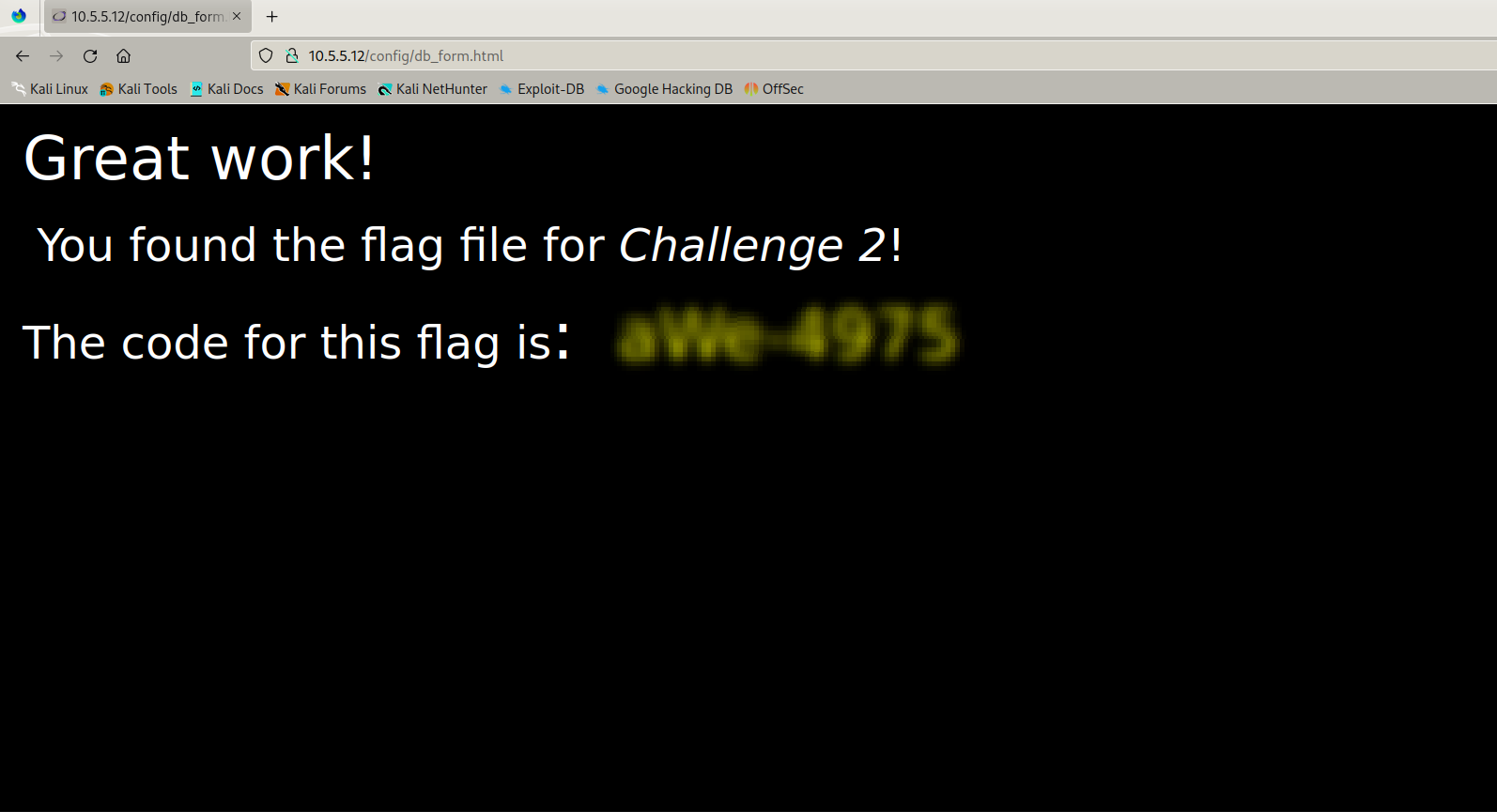
Step 8 — Retrieving the Challenge Code
Finally, I retrieved the challenge flag by navigating and accessing the exposed file directly:
/config/db_form.html
The file contained the Challenge 2 code.
Mitigation
To secure web servers against these attacks:
- Implement input validation and sanitization (reject
../,;, and other dangerous characters). - Use least privilege (restrict web server user permissions).
- Disable execution in upload directories.
- Regularly patch and update web applications.
- Monitor logs for suspicious requests.
Conclusion
This lab demonstrated how misconfigured and vulnerable web servers can be exploited using directory traversal, command injection, and file upload vulnerabilities. Proper hardening, monitoring, and secure coding practices are essential to defend against such attacks.